Image by Gerd Altmann, on Pixabay.
By James Myers
In 2004, the world celebrated the success of the Human Genome Project, which mapped about 92% of the human genome by identifying the precise order, or sequence, of the billions of DNA building blocks that make up human life. In recent years, next-generation sequencing (NGS) technologies have enabled scientists to decode, or sequence, much of the remaining 8%. However, while NGS has revolutionized medical treatment, disease screening, and ancestry information, it has also opened new risks for cyber-biosecurity over our most personal data: our DNA.
The human genome is the code for all genetic material in the human body, comprising combinations of organic molecules called nucleotides that wrap around each other to form the famous double-helix structure of DNA. Each nucleotide consists of one of four compounds that contain nitrogen, which are named cytosine, guanine, adenine, and thymine, typically represented by the letters C, G, A, and T. There are more than 3 billion of these four-letter combinations in differing sequences in the human genome.
A study published in IEEE Access this March, entitled Cyber-Biosecurity Challenges in Next-Generation Sequencing: A Comprehensive Analysis of Emerging Threat Vectors, warns of critical security gaps in NGS technologies that could expose personal genetic information to cyberattacks, espionage, and biological sabotage.
While cybersecurity weaknesses continue to plague millions of businesses and people who lose billions of dollars annually stolen from bank accounts and credit cards, the theft of genetic information can be particularly damaging because, unlike compromised credit cards, we can’t replace our DNA. A major data breach that occurred two years ago highlights the risk.
Two years after a major data breach in 2023, 23andMe continues to offer “nothing but the best” in its seasonal promotion for Christmas 2025.
In 2023, the ancestry-matching company 23andMe was hacked, and the genetic sequences of 6.9 million customers were stolen.
Since its founding in 2007, the California-based company has been collecting DNA samples from the saliva of customers, but the data breach led to its bankruptcy in March 2025. Although 23andMe continues to operate after being bought out by its former CEO, concerns about the security of customer information remain because as part of its bankruptcy settlement, the company is auctioning off the DNA profiles of 15 million people.
Twenty-seven U.S. states are suing the company to prevent the auction, while the company insists any buyer will be subject to the privacy conditions of 23andMe’s customer agreements.
Even if personal genetic information is publicly disclosed without identifying an individual by name, one test demonstrated that the data can be traced to a person with 84% to 97% accuracy by correlating it with public records and data purchased from brokers. (For more on the data brokering industry, see our December 2024 editorial Protecting Sensitive Financial Information From Data Brokers is a Crucial Government Responsibility). Once exposed, a person’s genetic data can be used for blackmail, discrimination, and fraud, among other possible abuses.

Image of the double-helix structure of DNA by Gerd Altmann, on Pixabay .
A particularly serious concern raised by experts in cyber-biosecurity is that synthetic DNA could, in theory, be used to carry malicious computer code.
Since DNA stores information in sequences of four chemical “letters,” it can be treated like a biological data system, like how computers store information in binary code. The complex structure of DNA, and particularly its double-helix formation, make it extremely resistant to errors and therefore very efficient for transmitting code in binary combinations, like typical computer code does. In 2018, researchers demonstrated that it was technically possible to hide malware within artificially created DNA. When the DNA was analyzed using next-generation sequencing (NGS) technology, the computer reading it became vulnerable to that hidden code. As computing power grows and DNA synthesis becomes cheaper, the risk of such misuse becomes more real.
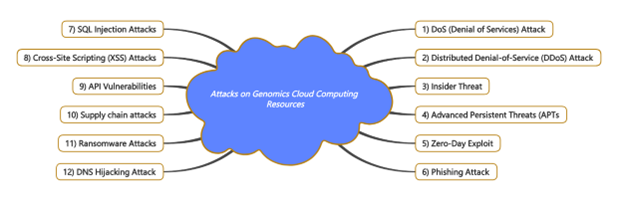
Figure 10 from the study Cyber-Biosecurity Challenges in Next-Generation Sequencing: A Comprehensive Analysis of Emerging Threat Vectors illustrates the risks of placing genomic data in the cloud.
The study’s authors identified 11 other methods by which sensitive genomic information could be compromised in NGS processes, including risks of placing genomic data in the cloud, and provided a detailed analysis for the implementation of each of the methods.
The authors call for several measures to protect the integrity and security of next-generation sequencing data. They include the development of ethical standards and comprehensive cyber-biosecurity frameworks that could involve the use of AI and machine learning to “analyse trends, discover anomalies in network traffic, monitor user activities, and assess system operations, facilitating the detection of potential security breaches prior to their occurrence.”
Other security measures could include fragmenting the NGS data and moving the data away from one potentially high-risk location and distributing it in parts on a wide network to reduce the concentration of risk. This might be accomplished with the help of blockchain technology, which would create a permanent record of data access and alterations. Each record in a blockchain is called a block, and each block in the entire blockchain system is linked by a secret code to every other block in the chain. The blockchain provides information on the time of each transaction and its order in a transactional sequence.
As technological capabilities rapidly advance, the authors note that “it is crucial to examine the possible effects of quantum computing on the security of genomic data. While quantum computing represents a substantial risk to current encryption standards, it simultaneously offers the potential to create novel and robust encryption methods capable of protecting sensitive genomic data.”
Lessons from the past can inform the future of cyber-biosecurity and DNA.
As it further develops, with the possibility of a major boost from the speed and accuracy of quantum computers, NGS technology holds promise for revolutionizing medicine and advancing human health. The study provides a wake-up call to researchers and the public, whose personal information is at risk, about the need for strong measures to prevent many possible types of technological abuse.
Public education could be added to the list of security measures. Cybercrime has become unfortunately commonplace and therefore too easily dismissed as inevitable, but the potential damage from the 23andMe data breach continues to threaten millions of the company’s customers. There is a particular threat to people of Ashkenazi Jewish and Chinese heritage, groups that appear to have been specifically targeted by the cybercriminals.
Can companies like 23andMe and the bidders on its data auction be trusted with such sensitive personal data as DNA, which we’re stuck with for life?
The lessons of the past can too easily be forgotten in the rapidly evolving technological world of today, but one event worthy of memory is 23andMe’s action to deprive customers of the right to class-action lawsuits by default. The company gave customers one month to opt out of a default provision to forfeit a legal right to class action, and it’s not difficult to imagine that many customers were unaware of either the opt-out option or the company-imposed deadline.
Further measures to protect DNA owners could include legal reforms that would give them more power in controlling the terms under which their DNA will be used.
As it now stands, few companies have been challenged on customer agreements, which are often dozens of pages long and full of legal terminology that’s beyond the reasonable knowledge of an average reader. It could be made a requirement that owners clearly understand what they’re agreeing to before the courts allow enforcement of the terms written by the companies. Highlighting key provisions relating to waivers of rights, court jurisdictions, and third-party use of data could be required in a short form of the agreement written in plain language.
If it’s not blocked by court action, 23andMe’s auctioning of DNA profiles amplifies the concerns published last year in our feature Legal Perils and Protections for Online Consumers are Rapidly Evolving. The risk to DNA owners underscores the importance of protecting our most precious data: our DNA.
Craving more information? Check out these recommended TQR articles:
- Thinking in the Age of Machines: Global IQ Decline and the Rise of AI-Assisted Thinking
- Everything Has a Beginning and End, Right? Physicist Says No, With Profound Consequences for Measuring Quantum Interactions
- Cleaning the Mirror: Increasing Concerns Over Data Quality, Distortion, and Decision-Making
- Not a Straight Line: What Ancient DNA Is Teaching Us About Migration, Contact, and Being Human
- Digital Sovereignty: Cutting Dependence on Dominant Tech Companies




