“A riddle wrapped in a mystery inside an enigma.” — Winston Churchill describing Russia on October 1st, 1939 during a radio address on the invasion of Poland by Germany and the Soviet Union.

Commercial sales brochure for the Enigma machine, 1925. Image: Dr. Enigma
By John Bamford
In February 1918, German electrical engineer Arthur Scherbius applied for German and English patents for an encryption machine based on rotating wired wheels, or rotors.

Arthur Scherbius, inventor of the Enigma cipher. Image: Wikipedia
He branded his product Enigma (Greek for “riddle”) in 1923 and marketed the machines primarily for commercial ciphering use and then to the German military, which initially showed little interest. That was the case until 1926, when the Enigma machines were first adopted by the German Navy and then by the German Army and Air Force.
And yes, it does look like an odd type of typewriter in a wooden box.
Understanding the Enigma ciphering machine and how to decode Enigma messages began in Poland, with the work of Marian Rejewski, Różycki and Henryk Zygalski.
First using permutation theory and flaws in German enciphering procedures, they were able to break message keys of the Enigma plugboard. The Polish Cypher Bureau bought a commercial version of Enigma in 1928, as reportedly did the British Foreign Office. While those machines were not identical to what would become the versions used by the German military, they supported the first steps in deciphering the workings of Engima. Key to this deciphering was an understanding of the wiring patterns used in the (initially) three rotors that Enigma used for encoding.
- A version of an Enigma enciphering machine. Image: Imperial War Museum, London.
- 1944 Enigma machine with four rotors. Image: National Museums Scotland.
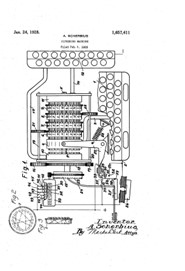
- Enigma ciphering machine patent US1657411A, United States Patent Office, by inventor Arthur Scherbius, filed 6 February 1923. Image: Wikipedia
The Enigma machine consisted of:
- A keyboard with a key for each letter of the alphabet;
- A set of rotors (initially 3 and subsequently up to 8) on a spindle, with each rotor having 26 electrical contact pins associated with each letter of the alphabet. These were the primary scrambling mechanism for letters;
- A stepping mechanism to turn at least one of the rotors when a key was pressed;
- A plugboard, on which each electrical plug was labeled with a letter of the alphabet, allowing wire cables to join letter pairs on the plugboard. The plugboard swapped those letters both before and after the main rotor scrambling unit;
- A lampboard with a lamp for each letter of the alphabet, and;
- A reflector mechanism that connected the outputs of the last rotor in pairs, redirecting electrical current back through the rotors by a different wiring route so that the machine would be self-reciprocating, allowing two machines that were identically set-up to either encrypt or decrypt messages.
Beginning with an initial setting for each of the rotors, and with the plugs initially wired between some combination of two letters, an operator would press a key and hold it to light a lamp indicating a letter of the alphabet. This was achieved by completing the various electrical circuits through the rotors and plugboard cables.
All of this provided formidable encryption, but there were flaws.
In the Enigma cipher:
- Letters never become themselves when encrypted, which was a limitation and technical flaw;
- The first transmissions of the day were often weather reports, which was a procedural flaw more than a technical one, revealing patterns in the code, and;
- Many messages ended with similar phrases, which was another procedural flaw that became useful when looking at a large volume of encrypted text, allowing some educated guesses to break the code. For example, the first portions of messages were often weather reports, and the last portion of messages was often “Heil Hitler.”
Building a Mechanical Cryptologic ‘Bomb’, Cyclometer, and Catalogue of Codes
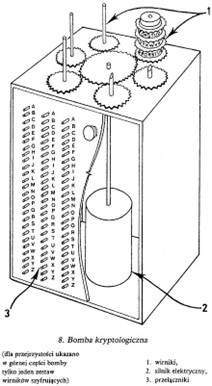
Diagram of Rejewski’s cryptologic bomb. For clarity, only one set of three rotors is shown (1); in reality, there were six such sets. An electric motor (2) turns the rotors to trigger (3) switches. Image: Wikipedia
The initial work by the Polish Cypher Bureau exploited some materials obtained by the French on daily encryption keys used by the Germans.
These included plugboard settings which, combined with message traffic and educated guesswork to solve the challenge of rotor wiring, allowed them to begin reading Enigma encoded messages by January 1933. This facilitated the design of mechanical devices to exploit characteristics of the rotors, to build a cyclometer and construct a catalogue with 100,000 entries. From this, they built an electromechanical cryptologic bomb (bomba in Polish) to search for rotor settings that could then be applied to Enigma coded messages for decoding. They created essentially their own version of the Enigma machine in the process.
Just prior to the German invasion of Poland in September, 1939, the Poles passed on to Britain and France all they had and knew about Enigma, including working Enigma replicas. But there were more challenges.
At midnight every day, the Enigmas in military use were reconfigured, adding many millions of possible configurations. The challenge was now to work out the continually changing machine set-ups. The task was aided by all the information and equipment obtained from the Polish Cypher Bureau, knowledge of Enigma from patents in Britain for both the commercial and military replica versions of the machine, as well as detailed information on the rotor wiring patterns being used by the military.
On 9 May 1941, the German weather-ship Munchen was attacked by the Royal Navy in the North Atlantic. Following standard orders, the Enigma machine it carried was thrown overboard, but other documents, including code books, were left onboard. These were recovered and sent to the British Government Code and Cypher School. These code books and others captured were key to understanding Enigma settings.

German ships were expected to throw Enigma machines overboard to avoid enemy capture, some of those have been found including this one found by Cristian Howe, Marine Biologist, Germany on the Baltic seabed. Image: arsTechnica
Alan Turing and Engineering of Probabilities With the Bombe

Alan Turing, 29 March 1951. Image: National Portrait Gallery, London
Alan Turing, born on 23 June 1913 in London, was a mathematician, logician, computer scientist, and, later, a cryptanalyst.
Turing began part-time work with the Government Code and Cypher School (GC&CS) in 1938. On 4 September 1939, with the United Kingdom having declared war on Germany, Turing began work at the GC&CS wartime facility at Bletchley Park, an estate in Buckinghamshire. There, he focused on understanding the workings of Enigma.
Soon after his arrival, having reviewed all of the Enigma-related information available, Turing specified an electromechanical machine called the “bombe” which was designed to deciper the Enigma code more effectively than the Polish bomba. Using a key enhancement called the “Diagonal Board”, suggested by mathematician Gordon Welchman, the self-reciprocity of the plugboard element of the Enigma was exploited. This enabled the bombe to solve the Enigma plugboard setting separately from the rotor setting, reducing the time required from days to hours to find the combined setting.
The bombe became the primary automated tool used to decipher Enigma messages.
It searched for possible correct settings, consisting of combinations of rotor order, rotor settings, and plugboard settings, that were used to encode an Enigma message. This was based on use of a fragment of text that might “fit” into the original message, such as the weather reports or common message endings, that were referred to as a “crib” (known plaintext attack, KPA). For each possible setting of the rotors, the bombe performed an electromechanical chain of logical deductions based on the crib. This was no mean feat, because of the huge number of possible states: for example, 3-rotor Enigmas had on the order of 190,000,000,000,000,000,000 possible states.
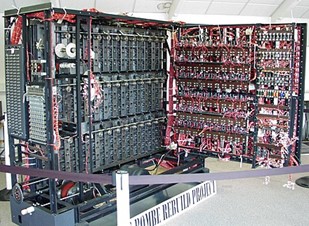
A working replica of a bombe, now at The National Museum of Computing on Bletchley Park. Image: Wikipedia
The first bombe was installed on 18 March 1940.
During processing, if the bombe encountered a contradiction, the particular setting was discarded and processing continued using the next setting. It was a time-consuming endeavour, facilitated by the bombe’s ability to process rapidly many potential settings. Most of the possible settings would cause contradictions and be discarded, leaving only a minority to be investigated in detail. A contradiction would occur when an enciphered letter would be turned back into the same plaintext letter, which was impossible with the limitations of Enigma.
A Testament to Human Ingenuity
Engineered and constructed at the height of German bombardments of English territory, with scarce resources and limited personnel, the bombe was instrumental in providing the Allied forces with advance information of Nazi military plans. The machine is credited with significantly shortening the war, causing great damage to German military assets, and saving potentially millions of lives.
The machine enabled not only codebreaking, but its advances in the applications of electrical engineering and mathematics set the stage for the introduction of Colossus, considered to be the world’s first programmable, electronic, digital computer.
The rest, as they say, is history as we know it.