Image generated using Ideogram AI.
By Mariana Meneses
The evolving landscape of technology presents a double-edged sword: Powerful advancements simultaneously threaten privacy and offer solutions against cyber-threats.
As outlined by the American Bar Association, pervasive data collection models and emerging technologies like facial recognition pose significant risks to individual privacy and democratic processes. However, amidst these challenges, there’s a growing recognition of the potential of technology to combat cyber-threats, from the development of sophisticated AI-driven security measures to the emergence of advocacy groups dedicated to safeguarding digital rights.
A recently-published study by HanXiang Xu and co-authors argues that the rapid development of Large Language Models (LLMs) is helping to improve cybersecurity by automatically detecting threats, analyzing malware, and responding to attacks. They conducted in-depth analysis of 127 top studies in the subject and showed LLMs being used for tasks like finding vulnerabilities, analyzing malware, and detecting network intrusions and phishing. However, the datasets for these tasks are often small and not sufficiently diverse. The authors highlight promising techniques like fine-tuning and domain-specific training for improving LLM performance in cybersecurity, and discuss challenges such as the need for protecting data privacy and the use of LLMs for proactive defense.
The study provides a detailed look at current research and future opportunities in using LLMs for cybersecurity.
In today’s digital world, protecting information and systems from cyber threats is more important than ever.
A 2024 study, authored by Taskeen Zaid and Suman Garai, proposes a new approach to cybersecurity called “deleakification,” which involves using a specialized virus to quickly find and remove leaked data from various systems. This method is faster and more effective than traditional techniques, especially for large amounts of data and hard-to-reach places like offline devices. However, using a self-replicating virus has significant risks, such as unintended data damage, privacy violations, and potential misuse for malicious purposes. The study also explores technologies that enhance data privacy by giving individuals more control over their information through decentralized identifiers and verifiable credentials.
These technologies reduce reliance on central authorities and improve security, but face challenges like technical complexity and adoption barriers. Overall, the study highlights both the potential and the risks of these innovative cybersecurity solutions, emphasizing the need for careful implementation and ethical considerations.
It’s crucial to recognize the disparities between entities capable of implementing cybersecurity measures and those facing adoption barriers.
A recently-published study conducted by Babajide Tolulope Familoni and Philip Olaseni Shoetan compares how two different and distant countries handle cybersecurity in a specific domain.
They investigate how the financial sectors in the US and Nigeria deal with cybersecurity challenges. More specifically, they examine the different ways these two countries protect their financial data from cyber threats. The study finds that the US has advanced technology and strong regulations but still struggles with complex cyber-attacks and insider threats. On the other hand, Nigeria faces problems like low awareness of cybersecurity, limited technology, and changing regulations. The authors conclude by arguing that despite these differences, both countries need to improve their cybersecurity measures.
The paper concludes that effective cybersecurity requires not just technology but also better regulations, increased awareness, and international cooperation, suggesting that each country can learn from the other’s experiences to better protect their financial systems.

Image generated using Ideogram AI.
As threats continue to evolve, it’s imperative to adapt security measures accordingly.
Evolving technologies such as artificial intelligence (AI), quantum computing, and the Internet of Things (IoT) are reshaping the cybersecurity landscape. AI can enhance threat detection by analyzing patterns and predicting attacks, but it also enables more sophisticated cyberattacks that can bypass traditional defenses. Quantum computing poses a future risk by potentially breaking current encryption methods, necessitating the development of quantum-resistant cryptography. IoT devices, while improving efficiency and connectivity, introduce numerous entry points for cyber threats due to their often-lax security measures.
Balancing the benefits of these technologies with robust security protocols is essential to mitigate their associated risks.
The World Economic Forum’s Global Cybersecurity Outlook 2024 – Insight report (pdf here) underscores several critical trends shaping the cybersecurity landscape.
One pressing concern is the growing disparity in cyber preparedness. This disproportionately affects small- and medium-sized enterprises (SMEs) and businesses in lower-income countries due to limited resources and cyber skills shortages, while larger organizations benefit from advanced technologies and training, exacerbating the gap.
Geopolitical factors also play a significant role, with heightened risks for global elections from misinformation, deepfakes, algorithmic manipulation, and other malicious acts. Additionally, the report highlights the dual nature of AI in cybersecurity, both enhancing defense mechanisms and empowering attackers through improved phishing, malware development, and sophisticated deepfakes.
Lastly, the persistent shortage of cyber skills, particularly in public organizations, poses a significant challenge to maintaining robust cybersecurity defenses. To address these issues, the report calls for increased collaboration and investment in cyber resilience, stressing the importance of all organizations achieving a minimum level of cybersecurity for a secure digital ecosystem.
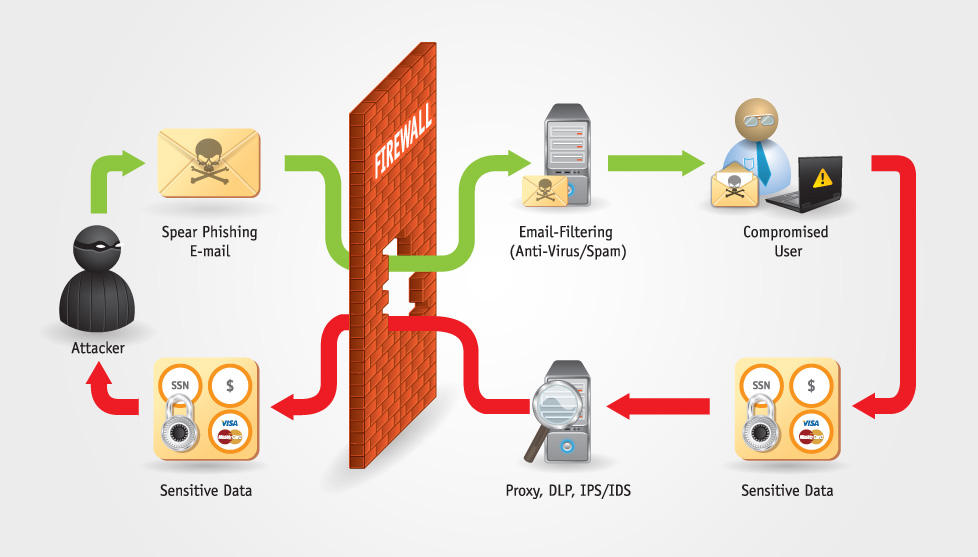
“Phishing is an attempt by cybercriminals posing as legitimate institutions, usually via email, to obtain sensitive information from targeted individuals.” (Phishing.org) Image: AbhaySingh1
The National Cyber Threat Assessment 2023-2024 by the Canadian Centre for Cyber Security highlights significant cybersecurity challenges today.
Key concerns include persistent ransomware attacks that disrupt services and cause financial losses, data breaches threatening personal and financial information, and misinformation spreading online. Essential services like hospitals and schools are particularly vulnerable. Emerging threats such as quantum computing, cyber espionage by nation-states, and vulnerabilities in AI and IoT devices also pose risks. The assessment emphasizes the need for collaboration and preparedness among government agencies, businesses, and international partners to protect against these cyber threats.
One example of a significant threat to digital privacy is the Pegasus spyware, which represents a highly invasive tool utilized by governments and private entities to breach personal domains and control digital devices.
The spyware’s “Zero-Click Exploitation” capability allows it to infect smartphones without user knowledge or action, granting access to a plethora of sensitive data including passwords, messages, photos, and even microphone and camera control. Its deployment against political activists, dissidents, and journalists, as documented by organizations like Amnesty International and Citizen Lab, underscores its chilling effects on free expression and human rights advocacy.
To reduce the risks, there are many organizations now working to empower people and protect their digital rights.
One of these organizations is the International Association of Privacy Professionals (IAPP), which was established in 2000 and is the leading global hub for privacy professionals. It offers conferences, research, training, certification, and networking for those in the data protection field. IAPP member and organizer Saima Fancy, a privacy advocate and AI ethics expert, has been at the forefront of discussions on the intersection of privacy and emerging technologies.
TQR had the privilege of interviewing Saima for the Quantum Feedback Loop podcast, focusing on “Why privacy matters on the road to AGI.”
Saima Fancy: Why Privacy Matters on the Road to Artificial General Intelligence
According to Cybercrime Magazine, the Anti-Phishing Working Group (APWG) “is the international coalition unifying the global response to cybercrime across industry, government and law-enforcement sectors and NGO communities.” They also feature the work of the Women in CyberSecurity (WiCyS), which is an organization dedicated to advancing women in the field of cybersecurity.
Based in San Francisco, The Electronic Frontier Foundation (EFF) is an international non-profit based that advocates for digital rights, privacy, and freedom of expression. Founded in 1990, the EFF focuses on protecting civil liberties in the digital age through legal challenges, support for open-source software, and initiatives on net neutrality and transparency. They propose to challenge invasive surveillance, defend against online censorship, and promote strong encryption. Engaging the public with educational resources and policy advocacy, the EFF aims to empower individuals to protect their digital rights.
Privacy International is a non-profit organization focused on advocating for privacy rights globally. Established in 1990, they campaign against surveillance and data exploitation by governments and corporations, aiming to protect individuals’ right to privacy in the digital age. They conduct research, engage in legal action, and raise public awareness about privacy issues, including mass surveillance, data breaches, and the impact of technology on human rights.

Image generated using Ideogram AI.
Given continuing rapid developments, there is an imperative to navigate the evolving landscape of cybersecurity and safeguard digital rights and privacy.
Recognizing the dynamic nature of cybersecurity, innovative approaches are being developed for threat detection, such as “deleakification” and the use of Large Language Models (LLMs). Additionally, technologies like AI, quantum computing, and the Internet of Things (IoT) present both opportunities and risks, emphasizing the need for a careful balance between innovation and security. Moreover, the disparities in cyber preparedness among different entities highlight the importance of collaboration and investment in cyber resilience.
In essence, there is an increasingly loud call for collective action to address cybersecurity threats while upholding fundamental rights and values in the digital age.
Craving more information? Check out these recommended TQR articles:
- Quantum Ethics: There’s No Time Like the Present to Plan for the Human Future with Quantum Technology
- From Nature to Robots and Vice-Versa? Blurring the Lines Between the Real and the Virtual
- The Observer Effect: Why Do Our Measurements Change Quantum Outcomes?
- Science Probes the Frontiers of Quantum and Mathematical Consciousness
- Remembering or Forgetting? Quantum Computing May Need Both